X2go and Ssh Ecdsa Keys
reading time: ~7m
Is x2goclient continuously asking you for enter passphrase to decrypt a key even when you absolutely know you’ve typed it correctly, or you already know the ssh key is handled by your ssh agent ?
Have you verified that your ssh key based login is working, via a terminal shell already ?
If yes, than read further to understand all about why x2goclient behaves that way and why I think this is a new bug in x2goclient.
First though, a short intro to x2go.
What is x2go ?
X2go is a remote desktop solution of sorts, it allows one to access a graphical desktop of a computer over a low bandwidth (or high bandwidth) connection http://wiki.x2go.org/doku.php/doc:deployment-stories:start [1]
X2go works in a server client architecture, with x2go server being installed on the systems to be accessed, and x2goclient being installed on the systems accessing the x2go server ( typically the x2goclients would be your workstations and laptops connecting to a shared/central x2go server )
X2go operates and competes in the same space as microsoft remote desktop, although uses a different wire transfer protocol tunneled through an OpenSSH encrypted connection ( see [1] ).
X2go can tunnel through the OpenSSH connection anything from the GUI on the server side, to sound and file transfers.
X2go is mostly meant to access Linux servers from clients running different OSes (Linux/Mac/Windows).
How does x2go help me ?
I have at home a very powerful desktop with plently of RAM and CPU cycles.
I run different kinds of headless virtualisation workloads on it ( mainly kvm and sometimes virtualbox ).
That being said I want to use the RAM and CPU cycles for the virtualisation workloads and not to run an Xorg GUI and a Desktop Environment.
Sometimes, the tools that work with virtualisation, have to be run with a GUI that the virtualisation provider provides, for debugging purposes ( think the virtualbox GUI or qemu/kvm GUI ).
Since I work through the terminal and via OpenSSH all the time, I naturally looked for a way of not having to run an entire Desktop Environment on my desktop all the time. I wanted to have the choice and flexibility of when to use a DE and when to not use a DE.
X2go allows me to spawn an entire KDE session when I use the x2goclient tool, run the necessary GUI debugging tools, then disconnect without needing to worry about turning off the DE on my headless desktop system. It is a handsoff way of running a DE only when you need to.
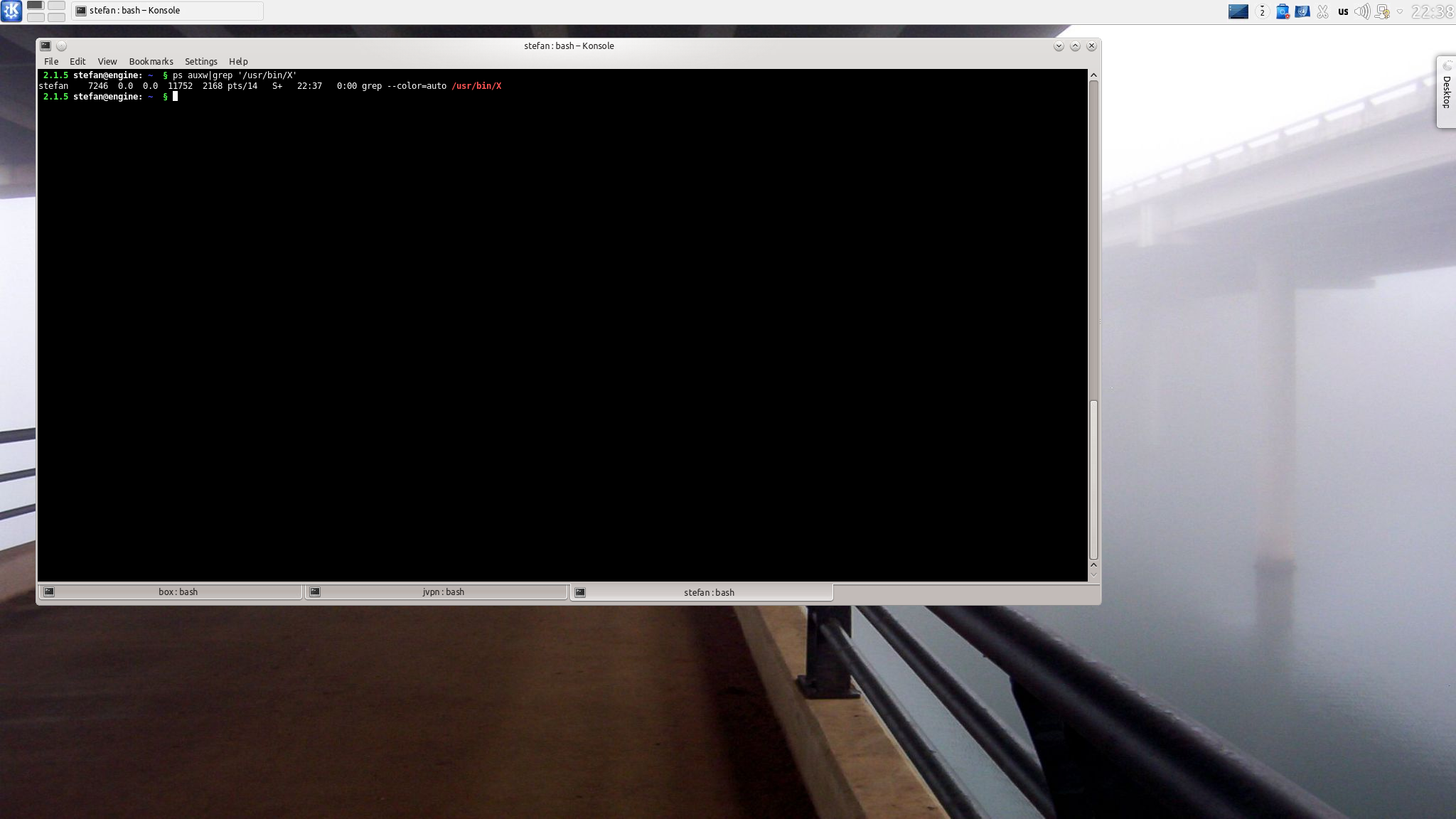
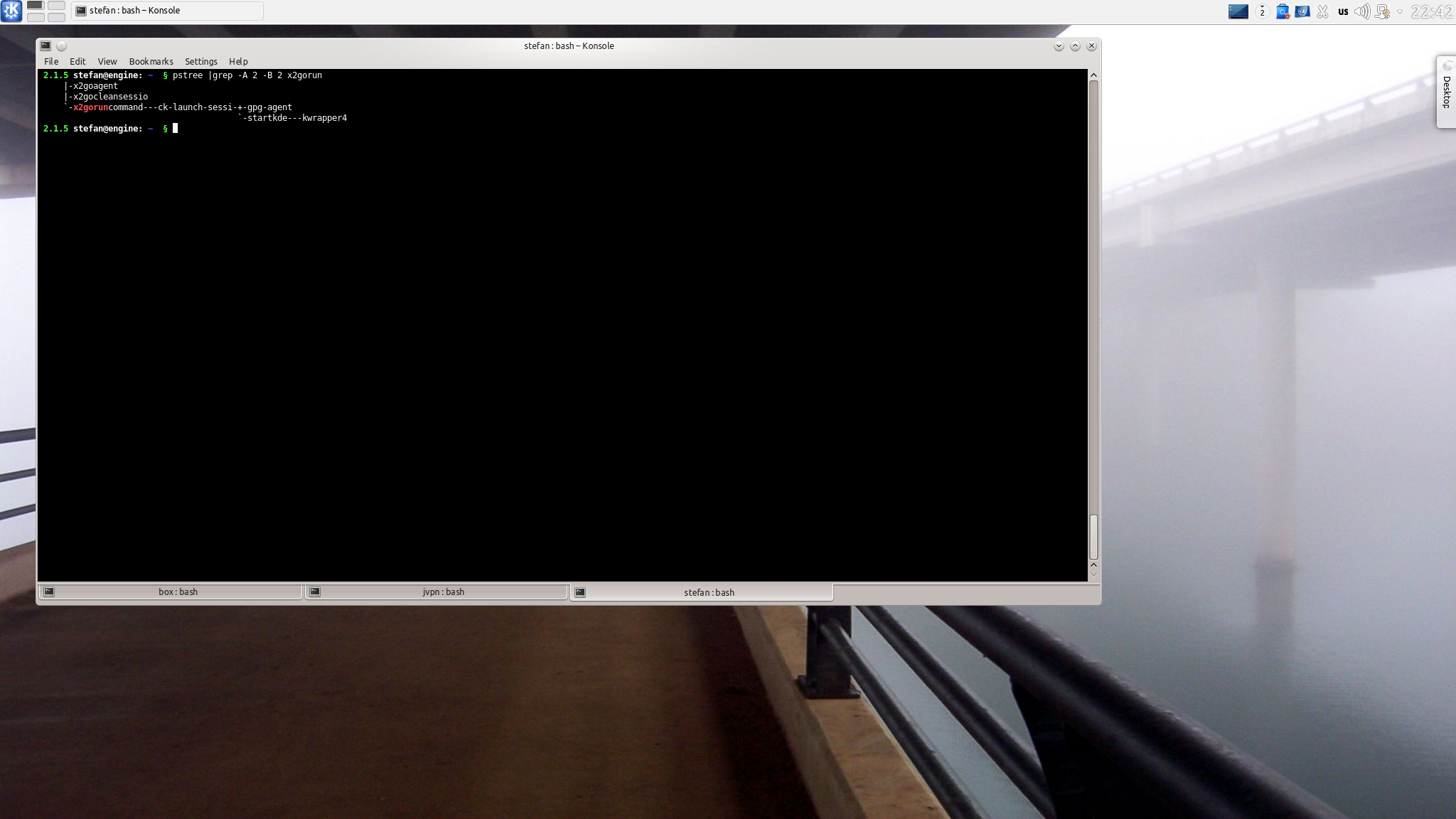
Now you’ll see 2 screenshots, capturing an x2go session, showing that there is no Xorg running, and that x2go starts a kde session.
The x2go bug
What is this x2go bug that I’m talking about ?
As it happens, x2go cannot use a private OpenSSH key of the ECDSA type using bcrypt as the passphrase hashing algorithm [2] [3]
I’ve tested this behaviour with both x2goclient nightly 4.0.5.1-0~1107~ubuntu14.04.1 and x2goclient stable 4.0.5.0-0~1099~ubuntu14.04.1 from a laptop running Ubuntu 14.04 amd64.
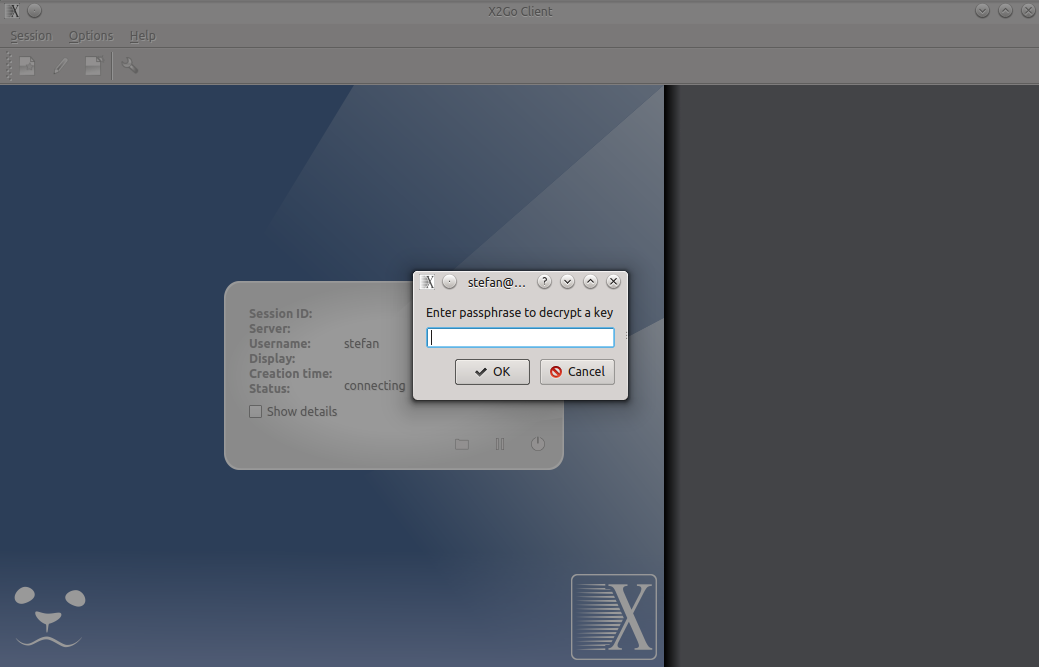
If I try to use the x2goclient with the ECDSA(bcrypt) type of ssh key I continuously get prompted to enter a passphrase to decrypt the key, even after typing the passphrase successfully x2go will continue the loop of asking for a passphrase. (see this screenshot)
The solution
The solution to this issue is very simple, once you’ve understood the problem :)
- Generate a second ssh keypair using RSA keys [4]
1 2 3 | |
- place the ssh public key on the x2go server
- test connectivity via a terminal ssh session
- instruct x2goclient to use the rsa key to connect
How do I know the difference between and ECDSA(with bcrypt) new style key and an old style RSA key I hear you ask ?
As it turns out the header of the ssh private key will tell you.
1 2 | |
1 2 | |
Comments
If you have any comments please use twitter, I’ve not enabled any comments on this blog yet.
Resources and inspiration
[1] - http://wiki.x2go.org/doku.php/doc:deployment-stories:start
[2] - https://wiki.archlinux.org/index.php/SSH_keys#ECDSA
[3] - http://www.tedunangst.com/flak/post/new-openssh-key-format-and-bcrypt-pbkdf